MACHINE LEARNING TECHNIQUES FOR REAL-TIME MALWARE DETECTION AND PREVENTION
DOI:
https://doi.org/10.71146/kjmr517Keywords:
Machine learning, Malware detection, Cybersecurity, Random Forest, Gradient Boosting, Support Vector Machine, Anomaly detectionAbstract
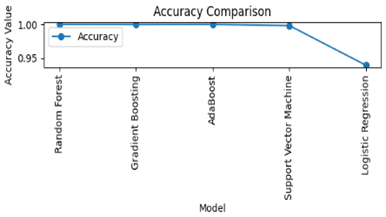
Viruses are dangerous and can weaken security besides costing a lot of money to any computer system in use today. The traditional techniques of malware detection including signature-based detection suffer from problems such as manual update, reactive approach toward threats, and scalability. This paper aims at analyzing the potential of applying machine learning in the detection of malware. Machine learning helps to detect new unknown types of malware because the program uses the data obtained and adapts to new threats. Based on three metrics features, this paper analyses the characteristics of Random Forest, Gradient Boosting, Support Vector Machine algorithms in malware detection. The results presented herein show that these models can enhance the detection rate, and offer Malware detection solutions that are both sustainable and flexible. This piece of research helps to enhance the methods for designing proper and effective cybersecurity.
Downloads
Downloads
Published
Issue
Section
License
Copyright (c) 2025 Muhammad Ali Saeed, Muhammad Abdur Raphay Zia, Naeem Aslam, Muhammad Fuzail, Muhammad Tanveer Meeran (Author)

This work is licensed under a Creative Commons Attribution 4.0 International License.






