INTELLIGENT INTRUSION DETECTION FOR ENHANCED SECURITY IN CLOUD COMPUTING
DOI:
https://doi.org/10.71146/kjmr329Keywords:
Cloud Computing Security, Intelligent Intrusion Detection, Principal Component Analysis (PCA), Machine Learning Algorithms, Threat Detection in Cloud, Adaptive Security MeasuresAbstract
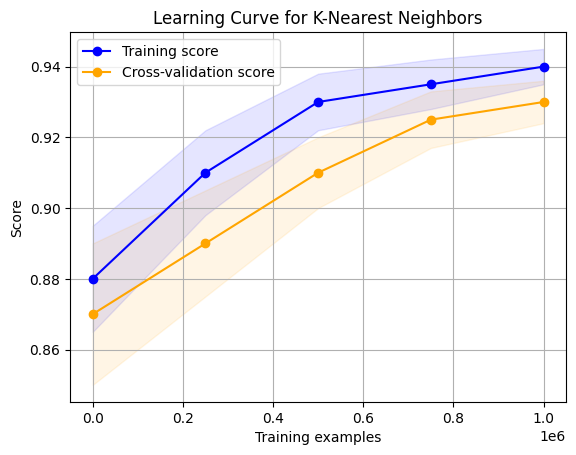
Advancements of cloud computing called for the storage of big data through the use of clouds but this came with a lot of risk. Thus, this thesis is aimed to manage these risks by proposing an Intelligent Intrusion Detection System (IDS) to improve cloud computing security. The experiments are based on the IoT Intrusion Detection dataset which contains different network traffic characteristics necessary to identify potential security threats including DDoS and MITM attacks. To classify network traffic as normal and intrusive, the following machine learning models are used, Support Vector Machines (SVM), Random Forest, K-Nearest Neighbors (KNN), Artificial Neural Networks (ANN). Both algorithms tested are analyzed by their accuracy in intrusion detection and the amount of time required to process the data appropriately for large-scale cloud computing systems. PCA is used for the purposes of dimensionality reduction and these make these models more efficient and faster by removing unnecessary variables in a dataset. This in a way helps the IDS to be able to process data with an emphasis on more significant aspects of a network intrusion. As for the effectiveness of the tested algorithms, it can be stated that Random Forest demonstrated the highest results both in terms of accuracy and the susceptibility to overfitting. Thanks to the ensemble method, which consists of using several decision trees, it provides high accuracy and computational efficiency in learning various patterns of data as well as high generalization compared to other datasets. This makes Random Forest particularly suitable in cloud based IoT systems where menace is always dynamic and random and threatens more often. the SVM has the highest accuracy rate in training context, has also been used in this study and has also been observed that this classifier has reached its highest training accuracy while its validation accuracy is significantly lower. This implies that SVM may not be good in generalizing to other data sets especially for real-time purposes in cloud security. KNN, though practical in the case of small matrices of measurements, illustrates the problem of data scalability that is critical where data is huge like in the case of cloud storage and computing. ANN works well and excels in recognizing intricate attacks’ patterns but it is sensitive to tuning and prone to overfitting, which is critical on big scale cloud data. Thus, the findings of the current study show that the use of machine learning in IDS methods advanced the detection of security threats in cloud environments. Applying all the criterions the Random Forest model shows the highest accuracy and generalization capacity and, therefore, is considered to be the best fitting for the real-world use in cloud-based IoT system. Not only does an event-type IDS identify previous attack patterns, but also it further learns new attack patterns by analyzing network traffic data of the network.
Downloads
Downloads
Published
Issue
Section
License
Copyright (c) 2025 Tanzeel-Ur-Rehman, Naeem Aslam, Muhammad Baqer, Muhammad Kamran Abid, Yasir Aziz, Muhammad Fuzail (Author)

This work is licensed under a Creative Commons Attribution 4.0 International License.






