AMalLSTM: ANDROID MALWARE DETECTION USING LSTM
DOI:
https://doi.org/10.71146/kjmr333Keywords:
Android malware detection, deep learning model, malware classifier, AMalLSTMAbstract
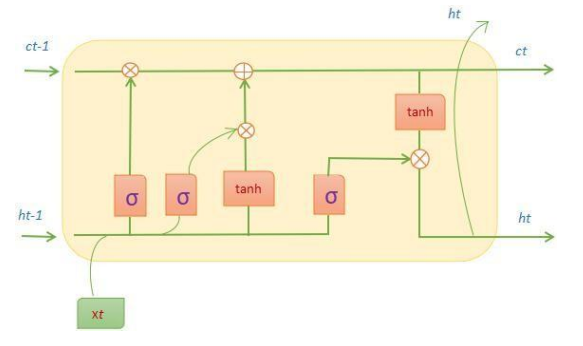
Android smartphone apps are becoming increasingly popular, but their security is a concern. Malware can cause damage to mobile devices and servers. Developing detection technologies to avoid attacks is crucial for protecting consumers' mobile devices, desktops, and servers. The goal of this study is to avoid malware attacks, which are addressed via static, dynamic and hybrid features. Combating such attacks requires effective malware detection tools. The framework restricts the deep learning architecture in order to find dependencies between APK-retrieved attributes. To examine the performance and robustness of our proposed system, we conducted a comprehensive experimental investigation that included machine learning and deep learning approaches. This study assesses the efficiency of LSTM for identifying Android malware appears in time-varying sequences of healthy and infected apps. To evaluate the AMalLSTM model, a set of malicious and benign Android applications, along with their package files containing features such as API calls, system call sequences, opcode sequences and permissions, are used. Nevertheless, the dataset has a balanced malware set for different types, but it does not cover the whole nature of Android malware and available tooling for producing new threats. Android malware classification accuracy is evaluated by means of deep learning models trained on the AMalLSTM framework. It works well on classification accuracy at low false positive and positive false negatives, thus being more favourable towards evasive virus tactics. The results demonstrate that the proposed approach exceeds earlier algorithms with detection accuracy: 98.4%, precision: 98.5%, recall: 97.2%, and F1 measure: 97.8%.Our future study is to apply LSTM network topologies to genuine Android malware samples, rather than static permissions or profiled program attributes.
Downloads
Downloads
Published
Issue
Section
License
Copyright (c) 2025 Mehwish Aslam, Ahmad Naeem, Ahmad Sarfraz, Muhammad Kamran Abid, Yasir Aziz, Naeem Aslam, Muhammad Fuzail (Author)

This work is licensed under a Creative Commons Attribution 4.0 International License.






