BLOCKCHAIN-BASED AUTHENTICATION FOR SECURE IOT NETWORKS: A DECENTRALIZED APPROACH TO IDENTITY MANAGEMENT AND DATA INTEGRITY
DOI:
https://doi.org/10.71146/kjmr556Keywords:
Blockchain, Internet of Things (IoT), Authentication, Data Integrity, Proof of Stake (PoS), Proof of Work (PoW), Scalability, Privacy Preservation, Consensus Mechanisms, Transaction Speed, SecurityAbstract
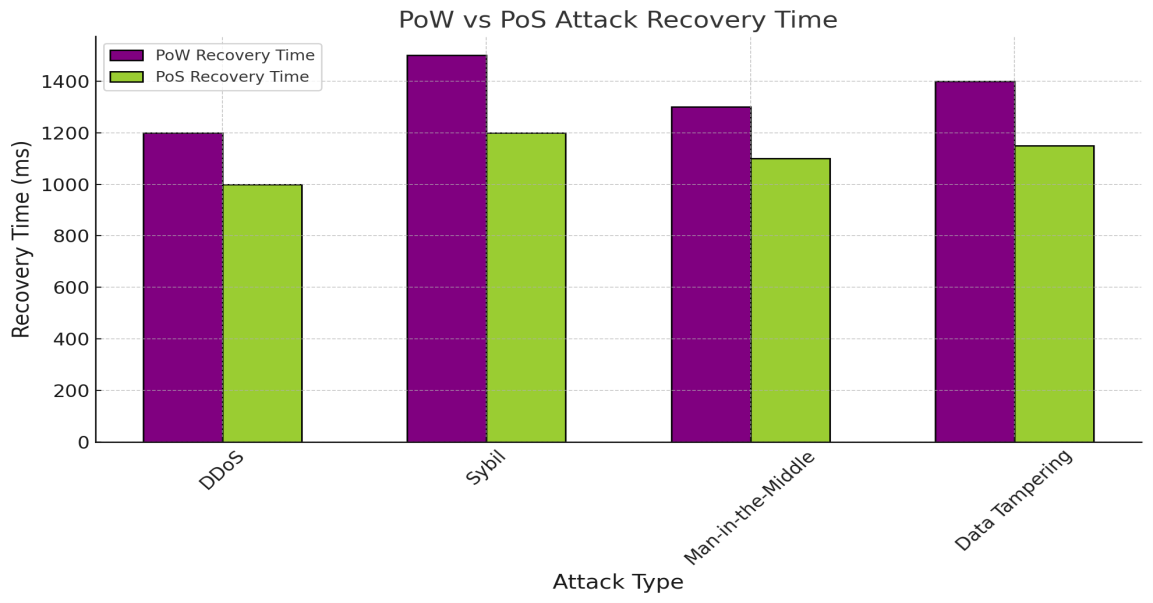
The growing popularity of the Internet of Things (IoT) networks has called out a growing need in sound and scalable security. The blockchain technology and its features of decentralization, immutability, and transparency can offer an effective solution to manage key security vulnerabilities, namely, authentication, data integrity, and privacy. This paper discusses the use of blockchain to IoT security, namely: decentralized authentication systems, data integrity management, and the challenge of scalability of large IoT networks. The findings indicate that despite the fact that blockchain can greatly improve security by guaranteeing data integrity and scheme-level device authentication, the performance of blockchain faced with output times of heightened issuance, slow transaction processing, and network constraints only emerge as network sizes rise. It has been proven that Proof of Stake (PoS) performs better than Proof of Work (PoW) regarding energy consumption, transaction latency, and time of recovery after failures due to attacks. Nonetheless, the paper underlines that streamlining blockchain protocols can help to mitigate performance stalls during massive IoT usage. The paper shows that, despite blockchain offering a secure basis to IoT, refinements in autonomous agreements, privacy safety nets, and scalability methods are required to make it an opportunity with broad IoT implementations.
Downloads
Downloads
Published
Issue
Section
License
Copyright (c) 2025 Rozina Chohan, Gulshan Naheed, Dr Khakoo Mal, Muhammad Jalil Afridi, Dr. Taha Shabbir, Dr. Saira Yamin (Author)

This work is licensed under a Creative Commons Attribution 4.0 International License.






